Keywords - SAAS, Private connectivity
Connect to services outside your VPC using private addresses as if the external service is within your VPC.
Uses Network load balancer to connect an interface VPC endpoint to a service.
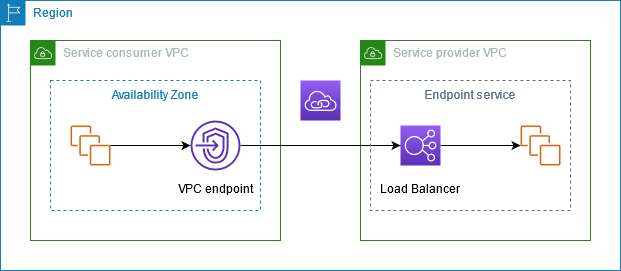
In service provider VPC (right) Create a VPC endpoint service (VPC > Endpoint services) which points to either a NLB or Gateway Load Balancer. The load balancer then forwards the traffic to the service compute. Assign a unique name to the service endpoint, consumers will need this name to connect. Share this with the consumer VPC account or Org. It can use multiple subnets across AZs to improve service resilience
In service consumer VPC (left) Create a VPC interface endpoint (VPC > Endpoints) and point to the endpoint service configured above.
A number of AWS Services support using VPC endpoints to keep traffic within the AWS network.
Useful to establish unidirectional connectivity from a consumer to provider.
Best suited for client/server kind of architectures. VPC range overlap is not an issue as the consumer ENIs are created such that it does not conflict with provider ENI.
Whitepaper https://docs.aws.amazon.com/whitepapers/latest/aws-privatelink/aws-privatelink.html #todo

Interesting read about how PrivateLink came to be? https://aws.amazon.com/blogs/apn/enabling-new-saas-strategies-with-aws-privatelink/