AWS Identity and Access Management (IAM) sandbox
Access Analyzer
https://aws.amazon.com/blogs/security/how-to-prioritize-iam-access-analyzer-findings/
In addition to roles, it also analyzes resource policies on supported resources
Monitors resources for external access AWS Simple Storage(S3) buckets AWS Identity and Access Management roles AWS Key Management Service Keys AWS Lambda functions and layers AWS Simple Queue Service queues AWS Secrets Manager secrets
Identity Center
SSO for Org
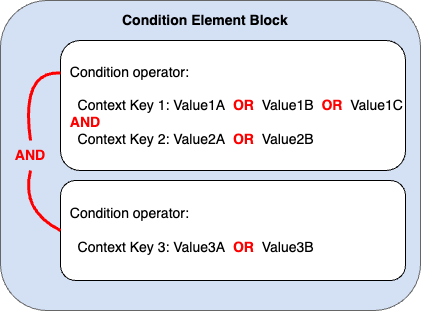
Policy Conditions
Useful to allow/deny actions based on certain conditions in addition to resource arn or patterns.
Can be used for ABAC
Tag based access control
Use the Service Authorization page to find which service or actions support which condition keys.
Context keys can be single valued or multi valued, more here
Evaluation logic - AND, OR conditions
Global Keys
These are available for most services and actions
All keys need an aws: suffix unless the prefix is specifically mentioned for a condition, liek ec2:RoleDelivery
| Principal | Example Value | Why use it? | Notes |
|---|---|---|---|
PrincipalArn | |||
PrincipalAccount | |||
PrincipalOrgPaths | |||
PrincipalOrgID | |||
PrincipalTag/TagKey | |||
PrincipalIsAWSService | |||
PrincipalServiceName | |||
PrincipalServiceNamesList | |||
PrincipalType | |||
userid | |||
username |
| Role Session | Example Value | Why use it? | Notes |
|---|---|---|---|
FederatedProvider | |||
TokenIssueTime | |||
MultiFactorAuthPresent | |||
Ec2InstanceSourceVpc | |||
Ec2InstanceSourcePrivateIPv4 | |||
SourceIdentity | |||
ec2:RoleDelivery | |||
ec2:SourceInstanceArn | |||
glue:RoleAssumedBy | |||
glue:CredentialIssuingService | |||
lambda:SourceFunctionArn | |||
ssm:SourceInstanceArn | |||
identitystore:UserId |
| Network | Example Value | Why use it? | Notes |
|---|---|---|---|
SourceIp | |||
SourceVpc | |||
SourceVpce | |||
VpcSourceIp |
| Resource Properties | Example Value | Why use it? | Notes |
|---|---|---|---|
ResourceAccount | |||
ResourceOrgPaths | |||
ResourceOrgID | |||
ResourceTag/TagKey |
| Request Properties | Example Values | Why use it? |
|---|---|---|
CalledVia | ||
CalledViaFirst | ||
CalledViaLast | ||
ViaAWSService | ||
CurrentTime | ||
EpochTime | ||
referer | ||
RequestedRegion | us-east-1 | Implement region deny controls by using this condition in an IAM policy or an SCP |
RequestTag/TagKey | Implement standard tags. Deny action if tag not present. Not all resources support request tags (RDS doesn’t!), so needs to be applied with other controls. | |
TagKeys | ||
SecureTransport | true, false | Implement encryption-in-transit by denying actions which do not have this enable. |
SourceArn | arn:aws:sns:us-east-2:123456789012:MyTopic | Use in a SQS queue resource policy to allow SNS to send message to the queue. Since principal is sns in this case, without the condition it can lead to the [[confused deputy problem]]. |
SourceAccount | ||
SourceOrgPaths | ||
SourceOrgID | ||
UserAgent |
Refer AWS docs
Examples
Not working
"Condition": {"StringEquals": {"aws:TagKeys": ["Department"]}}
Working
"Condition": {"ForAllValues:StringEquals": {"aws:TagKeys": ["Department"]}}
Working
"Condition": {"ForAnyValue:StringEquals": {"aws:TagKeys": ["Department"]}}
Managed Policy
Refer https://docs.aws.amazon.com/aws-managed-policy/latest/reference/policy-list.html