AWS Direct Connect incubating
While VPN connections are OK, for some critical workloads, VPN over internet may not be stable or available enough.
If a customer doesn’t want to connect to AWS over the internet, they can alternatively use Direct Connect. This ensures the traffic to/from AWS flows through the customer’s network directely on to AWS backbone network without going over the internet.
Cost effective, secure, performant private network connectivity between on-prem private network and AWS.
Location
These are the AWS provided physical locations customers connect their on-prem data centers to, to establish direct connectivity with AWS back bone network.
All such locations have a default region associated with them depending on their location. However, the Direct Connect connection established using a particular location can be used for any region (except some exceptions for China).
Some locations support MACSec for some port speeds (mostly for 10 and 100 Gbps). Most widely available port speed is 10 Gbps which is offered at every location, unlike 1 Gbps and 100 Gbps which some locations don’t support.
Connection
Establish a connection to AWS Direct Connect location.
Dedicated
A physical ethernet connection associated with a single customer, can be a 1 Gbps, 10 Gbps, or 100 Gbps Ethernet port.
Hosted
A physical ethernet connection privisioned by an AWS partner for a customer. Only supports ONE [[#Virtual Interface (VIF)]]
Virtual Interface (VIF)
A virtual interface is the VLAN that transports Direct Connect traffic. It can be connected to either a Virtual Private Gateway (VGW) on a VPC, or Direct Connect Gateway (DXGW)
If connected to a VGW, it enables connectivity to a single VPC in a single region.
If connected to a DXGW, it enables connectivity to multiple VPCs, across regions.
Private Virtual Interface (Private VIF)
Access Amazon VPC resources using private IP addresses.
Public Virtual Interface (Public VIF)
Access AWS public services using public IPs.
Transit Virtual Interface (Transit VIF)
Transports traffic from a Direct Connect Gateway (DXGW) to one or more Transit Gateway.
Only available for Dedicated or Hosted connection with speeds of 1 Gbps or more.
Direct Connect Gateway (DXGW)
Use DXGW to connect Direct Connect connection to one or many vpc over a Private Virtual Interface (Private VIF)
You can attach multiple Private VIF to a DXGW, this enables North-South connectivity (between on-prem and AWS) BUT does not enable East-West connectivity (between VPCs on AWS).
This is strictly for private connectivity. You cannot connect a Public Virtual Interface (Public VIF) to a DXGW.
Connection Patterns
[!info] Q The DXGW is a control plane-only device. In other words, no actual traffic goes over it, it is just a Route-Reflector, it only carries the routing table.
Source - AWS Blog
Questions
The DXGW is a control plane-only device. In other words, no actual traffic goes over it, it is just a Route-Reflector, it only carries the routing table?
Given the above, what physical medium does the traffic use? And how does it compare to the Transit Gateway?
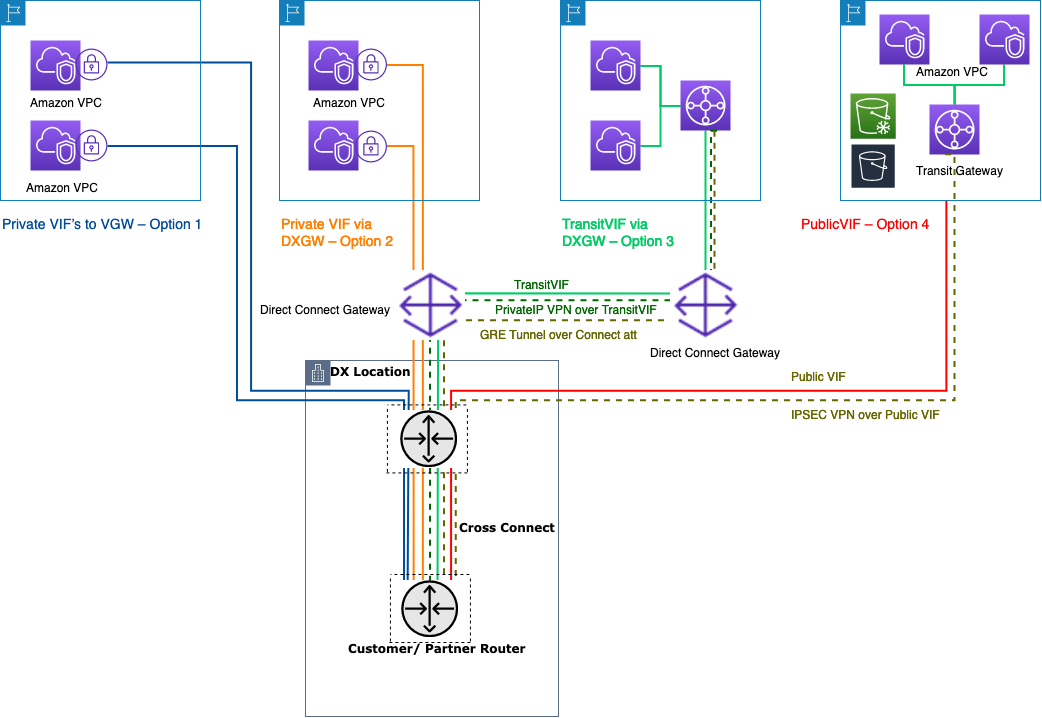
Connect DC location to VGW over Private VIF
1 virtual interface can connect to only 1 VPC (via virtual-private-gateway) 1 direct connect connection supports max 50 VIF 1 BGP peering session per VPC. Region specific to Direct Connect region.
Connect DC location via DXGW to VGW over Private VIF
Direct Connect Gateway (DXGW) is a global resource. It can connect to upto 10 VPCs (via VGW) over 1 VIF. It allows North-South (on-prem to AWS) connectivity but not East-West (between VPCs). 1 BGP peering session per DXGW per Direct Connect connection. Good fit if the size of the landing zone on AWS is small, less than 10 VPCs.
Connect DC location via DXGW to TGW over Transit VIF
Use Transit Virtual Interface to connect Direct Connect Gateway to Transit Gateway.
1 DXGW can connect upto 3 TGW over 1 Transit VIF. Simplest, scalable setup to establish reliable connectivity with AWS without going through the Internet. TGW can only advertise 20 Prefix over the Transit IVF to on-prem router. Cost = Direct Connect pricing + TGW attachment + TGW data transfer charges
Connect DC location via VPN to TGW over Public VIF
Use to encrypt your Direct Connect traffic at Network layer.
The Public VIF advertises all AWS public IP to on-prem router including the public IP of VPN endpoints created when adding a VPN attachment to Transit Gateway.
Advisable to use some firewall routing at the on-prem router since AWS advertises all public IP ranges.
Connect DC location via GRE tunnel to TGW over Transit VIF
Use Transit Gateway Connect attachment type to connect on-prem SD-WAN virtual appliances directly to Transit Gateway without IPSec VPN using GRE tunnel. This enables high bandwidth performance compared to a VPN.
Which pattern to pick?
Decide based on the requirements, and the advantages/disadvantages of each pattern.
The simplest (not cheapest) approach is to use the 3rd pattern. Connect DC location via DXGW to Transit Gateway over Transit VIF. This helps centralize all your connectivity needs to a single Transit Gateway.
Consider the 1st pattern, connecting to a VPC directly using a private VIF for large amounts of data transfer. This will save Transit Gateway data processing charges applicable when using the 3rd pattern.
Consider using the 4th pattern, Transit Gateway Connect + GRE tunnel to connect the on-prem SD-WAN appliances/infrastructure to AWS without VPN.
Resilience
To maintain production grade resilience, it is recommended to use at-least 2 Direct Connect connections terminating at 2 appliances/devices in each of 2 different customer sites. This provides 4 connections in total with a high degree of resilience.
For development workloads, you can configure 2 connections terminating at 2 appliances/devices at a single customer site.
Backup Connection
It is also advisable to have a high performance backup connection to the Direct Connect connections.
Virtual Private Gateway (site to site VPN) is a simple pattern to enable backup connectivity between customer sites and AWS. However, due to limited bandwidth of 1.25 Gbps/tunnel, and no support of ECMP, it is generally not favoured.
To maintain high performance over the backup connection, it is advisable to use Transit Gateway VPN which supports ECMP. Even thought the individual tunnels still operate at 1.25 Gbps speeds, due to ECMP, it is possible to achieve much higher speeds.